Unified Attack Path Management
GEIGER — See every attack path across AD, Azure, AWS, GCP, Okta, and Kubernetes
Security teams juggle 25-50 different tools. Critical attack paths slip through the cracks because they span multiple tools that don't talk to each other.
Geiger changes that. Active Directory, Azure, AWS, GCP, Okta, and Kubernetes identities in a single graph database. Attack paths calculated in seconds, not hours.
Request Attack Path Assessment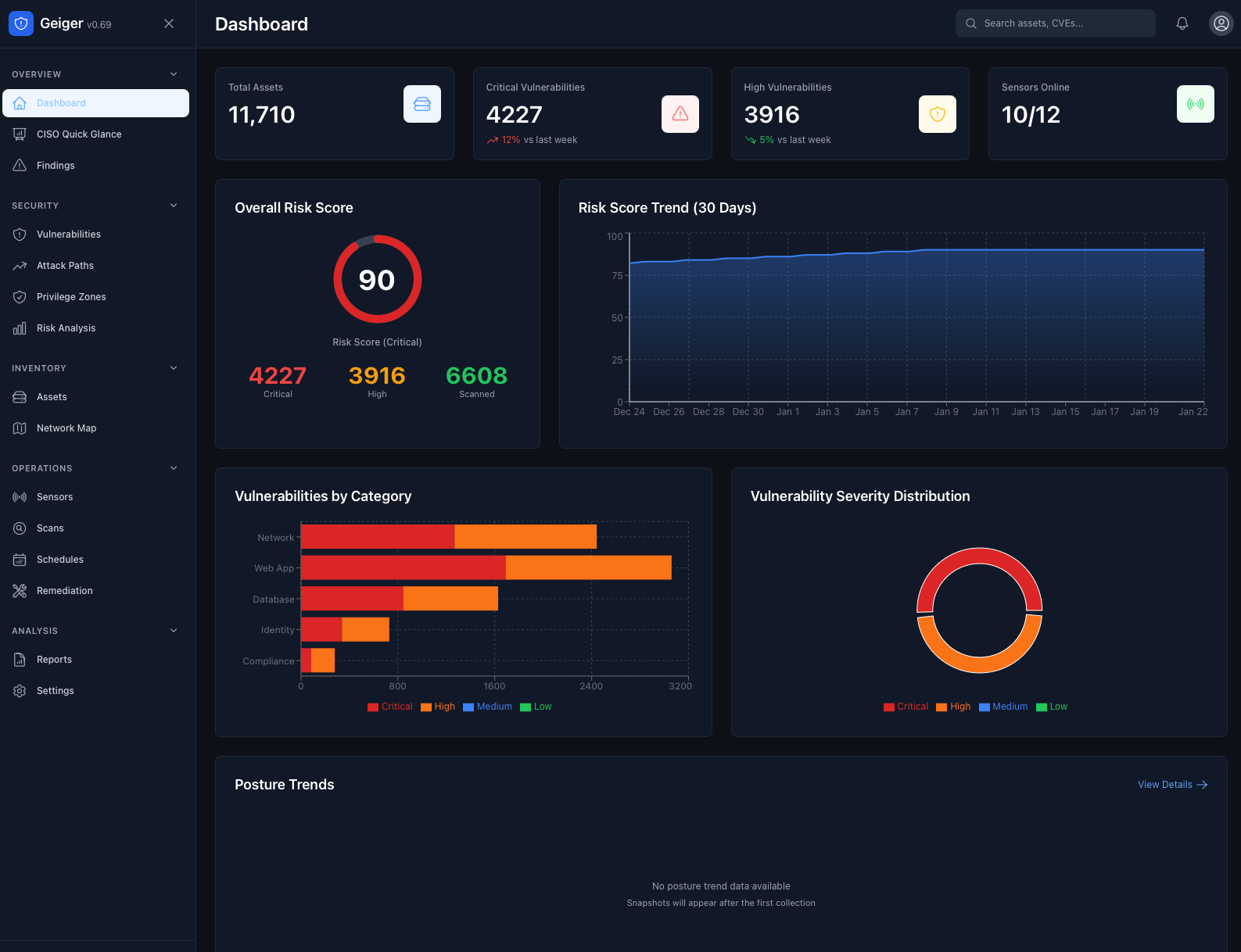
Your Tools Don't Talk to Each Other
A compromised service account in Azure with lateral movement paths to on-prem Domain Admins? That requires correlating data from at least three different tools.
By the time you've exported, normalized, and cross-referenced the data, an attacker has already completed the attack chain.
Geiger sees the complete picture.
Find Every Path to Your Crown Jewels
Geiger identifies all attack paths to your most critical assets. 50+ pre-built queries. One click to see every user, group, or service account with a path to Domain Admins, Azure Global Admin, or your custom high-value targets.
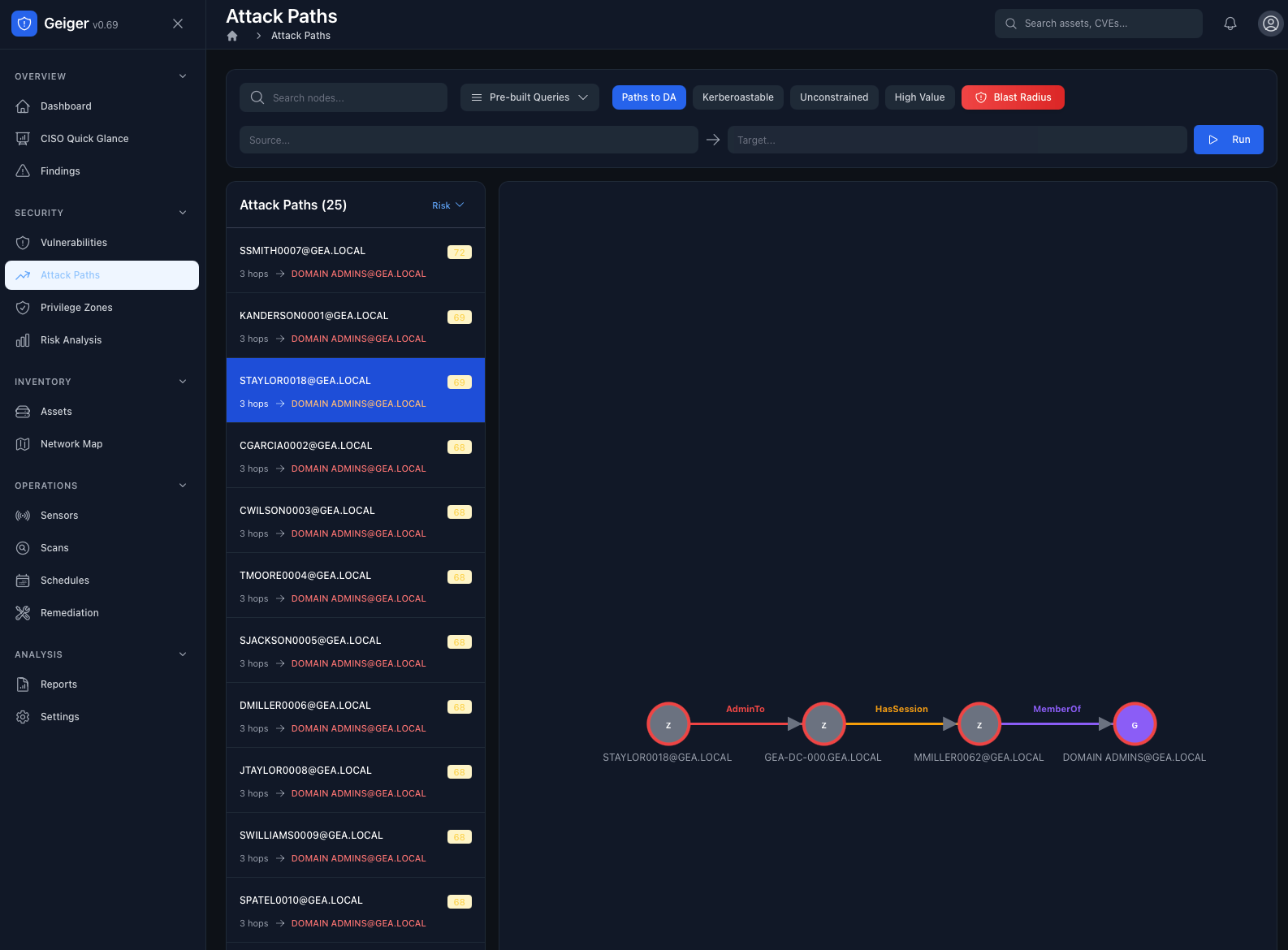
Blast Radius Analysis
What happens if this account is compromised? Geiger calculates the blast radius instantly. See every asset reachable from any starting point, the maximum depth of the attack chain, and which high-value targets are at risk.
- Impact score calculation
- Total assets in blast radius
- Critical assets at risk
- Maximum attack depth
- High-value target identification
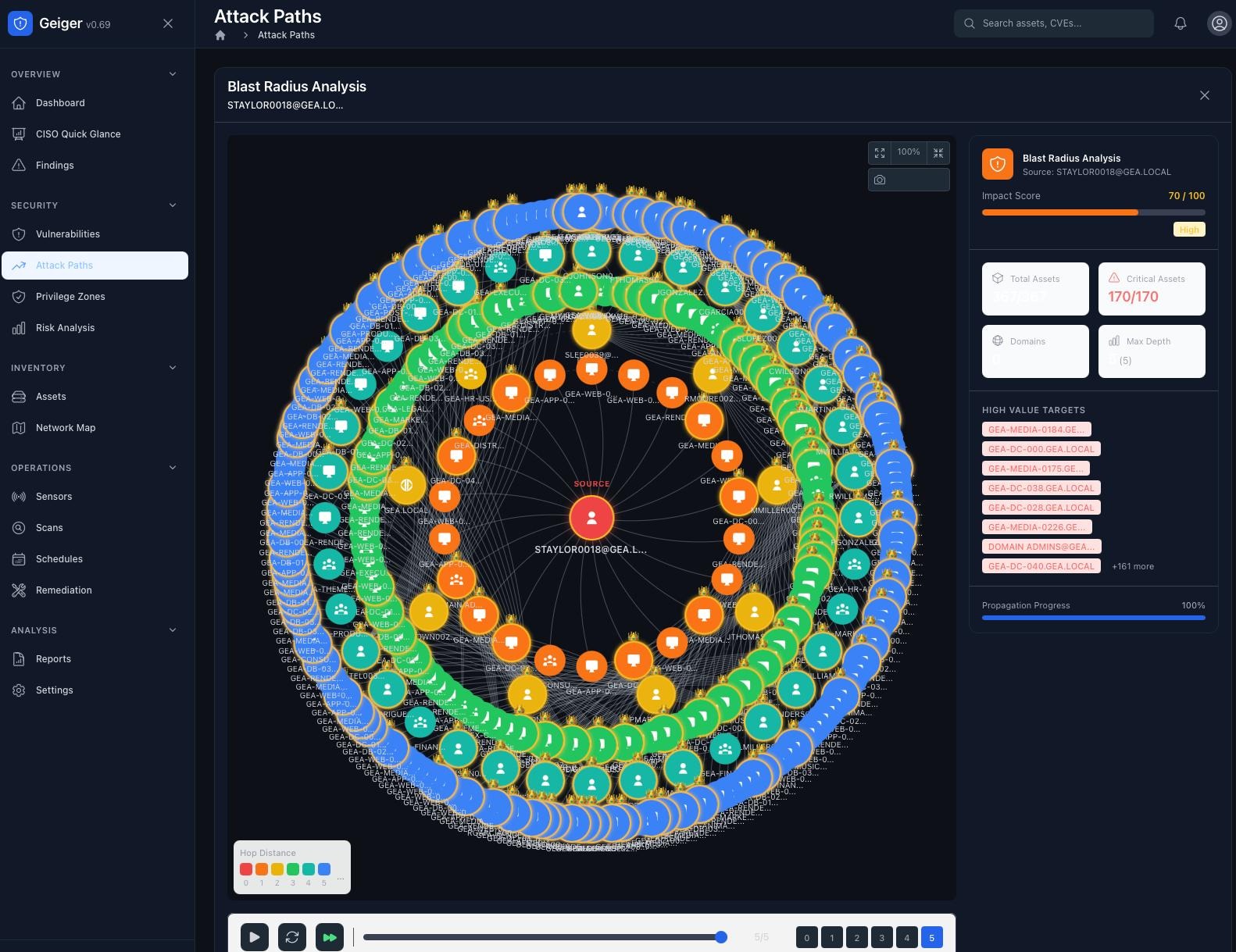
Complete Identity Visibility
Identity data from across your entire environment, unified in a single graph database.
Active Directory
- •Users, Groups, Computers, OUs, GPOs
- •Trusts, ACLs, Kerberos delegation
- •ADCS certificates
Azure / Entra ID
- •Users, Groups, Service Principals
- •Applications, Roles, Devices
- •Subscriptions
AWS IAM
- •Users, Roles, Policies
- •Trust relationships
- •EC2 instances, KMS keys
GCP IAM
- •Service Accounts, Roles
- •IAM Bindings, Projects
- •Compute resources
Okta
- •Users, Groups, Applications
- •MFA status, API tokens
Kubernetes
- •Service Accounts, Roles
- •RoleBindings, ClusterRoles
- •Namespaces
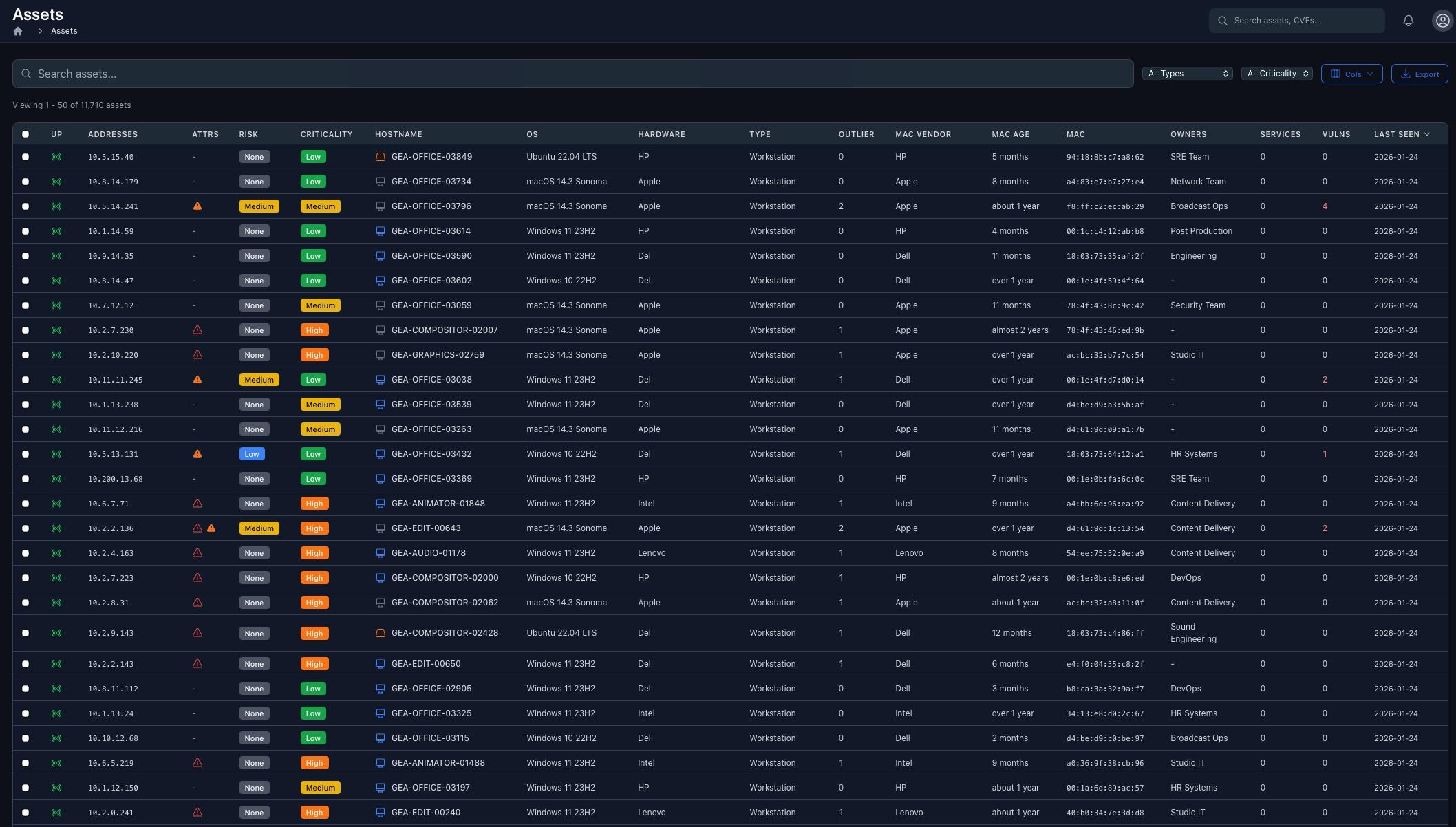
Complete Asset Inventory
Every asset across your environment in one view. Filter by criticality, risk, hardware, OS, services, and vulnerabilities. Track MAC age, ownership, and last seen timestamps.
Risk-Based Prioritization
Not all attack paths are equal. Geiger's risk scoring considers:
- Path length - Shorter paths are more exploitable
- Edge types - DCSync is worse than CanRDP
- Target criticality - Domain Controllers vs workstations
- Source context - Paths from compromised accounts are urgent
- Business impact - Test server vs payment systems
The result: A prioritized list of what to fix first, not 10,000 equally-weighted findings.
Privilege Zone Enforcement
Define your security boundaries:
- Admin Zones - who should have elevated access
- Production Zones - which identities can touch production
- Staging/Dev Zones - environment separation
- Custom Zones - your own boundaries
When an identity violates zone boundaries, Geiger alerts immediately.
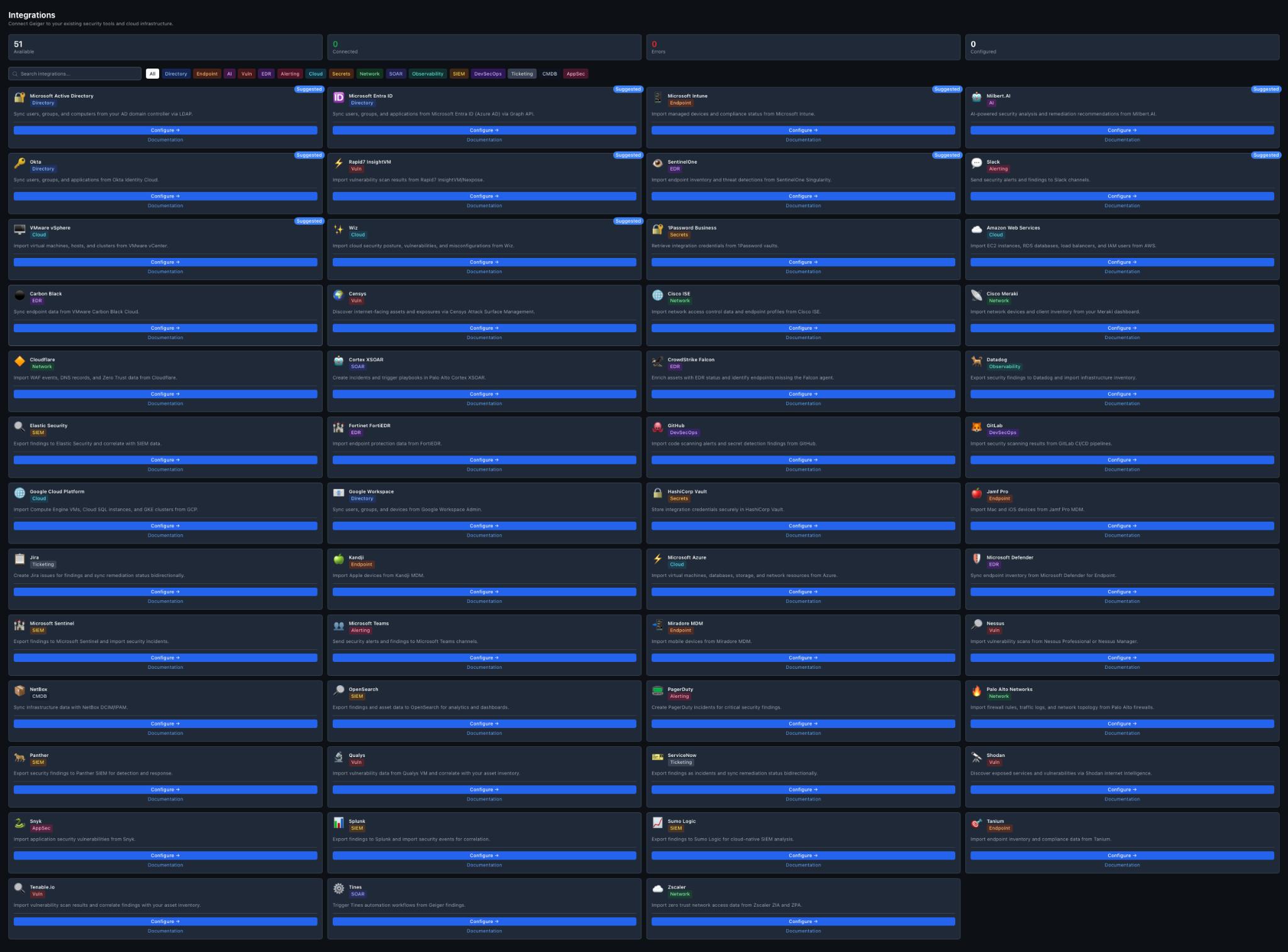
51 Integrations
Connect Geiger to your existing security tools and cloud infrastructure.
Remediation That Drives Action
Findings don't sit in a dashboard. Geiger drives action.
Step-by-Step Guidance
Remediation instructions for every finding type
Jira & ServiceNow
Automatic ticket creation and tracking
Verification
Track from open to verified-fixed
Risk Acceptance
Workflows with automatic expiry
Posture Trending
Prove security improves over time
Full API Access
200+ REST API endpoints
Technical Architecture
Part of the ThreatHunter.ai Ecosystem
GEIGER is powered by the ARGOS platform and backed by expert threat hunters who use attack path data to proactively hunt for compromise.
ARGOS Platform
The backbone of all ThreatHunter.ai services. Unlimited data sources, real-time processing, and AI-powered analysis.
MILBERT
Pair attack path analysis with AI-powered identity threat detection to catch active exploitation of discovered paths.
24/7 Threat Hunting
Human analysts use GEIGER findings to prioritize hunts and validate whether attack paths are being actively exploited.
Frequently Asked Questions
What is attack path management?
Attack path management maps the routes an attacker could take from initial access to your most critical assets. GEIGER visualizes these paths across AD, Azure, AWS, GCP, Okta, and Kubernetes in a single graph.
How is GEIGER different from BloodHound?
GEIGER unifies identity data from six platforms in one graph database with 50+ pre-built queries, risk-based prioritization, and remediation workflows including Jira and ServiceNow integration.
How often does GEIGER scan?
GEIGER continuously collects identity data through distributed sensors. Scans can be scheduled or run on demand, with changes tracked over time.
Does GEIGER require endpoint agents?
No. GEIGER uses distributed sensors that connect to your identity providers and cloud platforms via API. No endpoint agents are required.
See Your Attack Paths
Schedule a demo to see how Geiger maps your identity infrastructure and prioritizes your highest-risk attack paths.
Request Attack Path Assessment