Vulnerability Management with Real Risk Scoring
TACT-IO — Tactical Threat Assessment & Continuous Threat Intelligence Operations
Stop chasing vulnerabilities. Start eliminating risk.
22,000+ new vulnerabilities discovered each year. Legacy scanners generate noise, not insights. TACT-IO's Real Risk Score surfaces the 5% of vulnerabilities that pose 95% of your risk. One platform. Complete visibility. Intelligent prioritization.
Request Vulnerability Assessment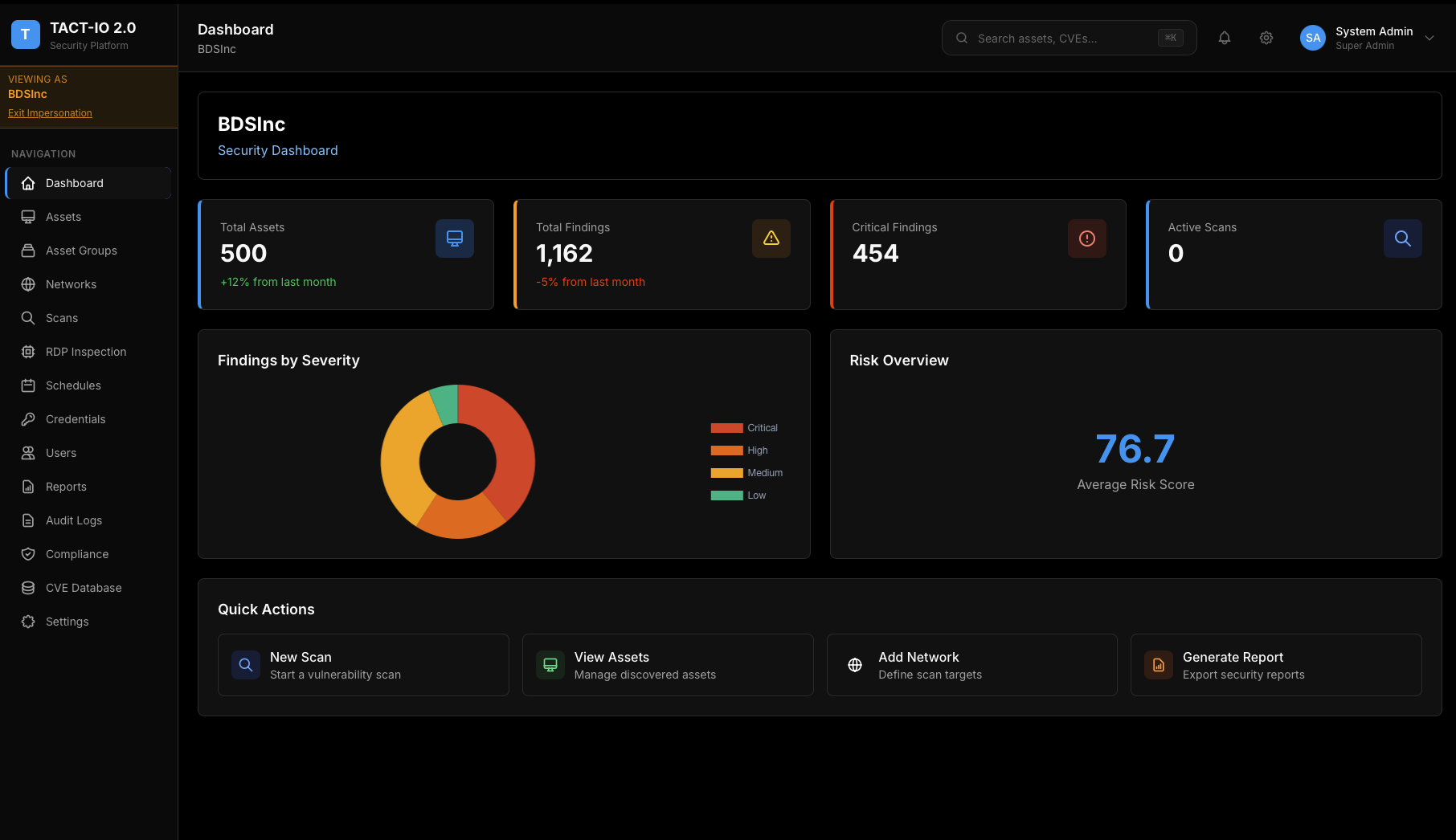
The Problem is Clear
22,000+
New vulnerabilities discovered each year
40%
Of team time spent correlating data across tools
60%
Of breaches exploit known, patchable vulnerabilities
Legacy vulnerability scanners generate noise, not insights. They tell you what's wrong but not what matters. A CVSS 9.0 vulnerability on a development laptop gets the same priority as one on your production database.
TACT-IO knows the difference.
The TACT-IO Difference
Result: 80% reduction in remediation workload while improving security posture.
| The Old Way | The TACT-IO Way |
|---|---|
| 2,500 critical findings | 125 true priorities |
| CVSS-only severity | Multi-factor Real Risk Score |
| Point-in-time snapshots | Continuous monitoring |
| Separate compliance tools | Unified platform |
| Manual correlation | Automated intelligence |
Real Risk Score: Intelligence, Not Just Data
Not all vulnerabilities are equal. TACT-IO's proprietary Real Risk Score combines seven intelligence sources to surface the vulnerabilities that actually threaten your organization.
CVSS Base Score
Vulnerability severity assessment
EPSS (Exploit Probability)
Probability of exploitation in next 30 days
CISA KEV
Known exploited in the wild
Exploit Availability
Public exploit code exists
Asset Criticality
Business impact weighting
Network Exposure
Internet-facing vs internal-only
Vulnerability Age
Time since disclosure
The Result?
Focus on the 5% of vulnerabilities that pose 95% of your risk.
95%
Reduction in critical findings
<5%
False positive rate
4x
Faster remediation
<1hr
Time to identify critical exposure
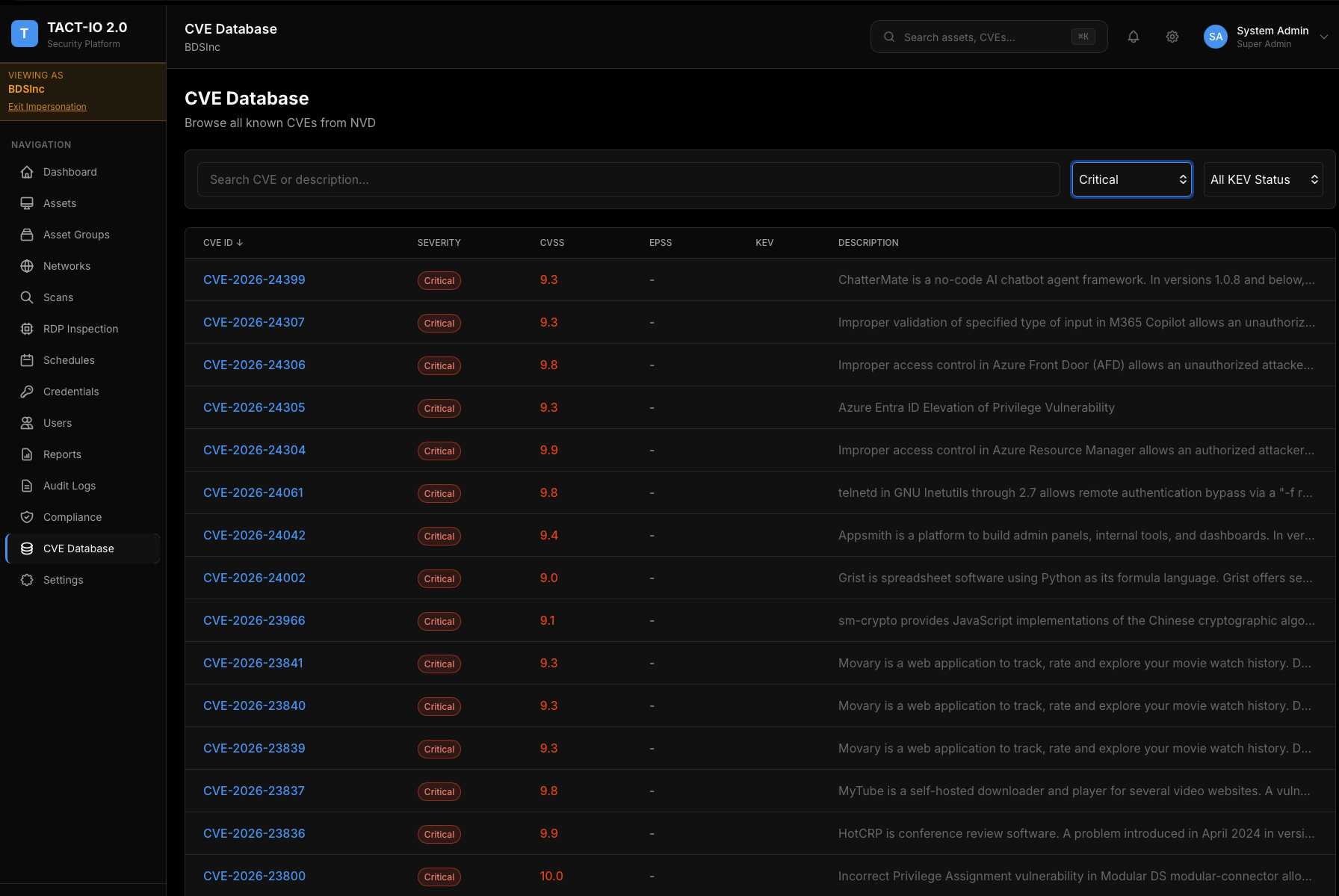
Complete CVE Database
Browse all known CVEs from NVD. Filter by severity, search by description, and track KEV status. Every vulnerability correlated with EPSS exploit probability.
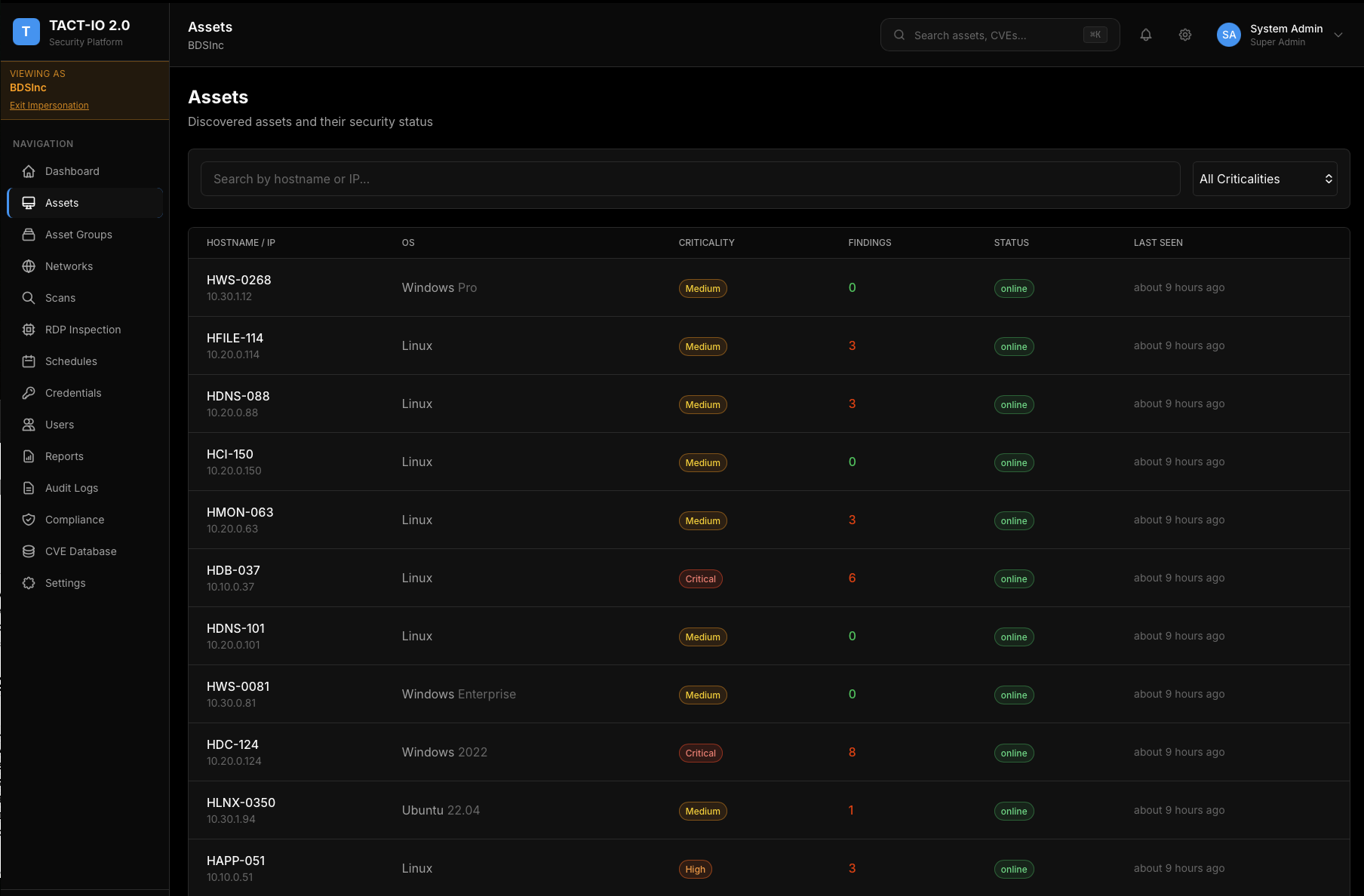
Complete Asset Visibility
Continuous asset discovery across your entire environment. Every asset tracked with OS, criticality, findings count, and security status.
- Continuous Discovery - Network scanning, cloud API integration, agent-based
- Asset Criticality - Business impact weighting for prioritization
- Hierarchical Groups - Unlimited nesting to match your org structure
- Dynamic Groups - Rule-based automatic membership
Enterprise-Grade Scanning
Distributed scanner architecture with intelligent clustering, automatic failover, and geographic distribution.
Vulnerability
Unauthenticated vulnerability detection
Authenticated
Deep inspection with credentials (Windows WMI, Linux SSH)
Full Assessment
Complete security audit combining all scan types
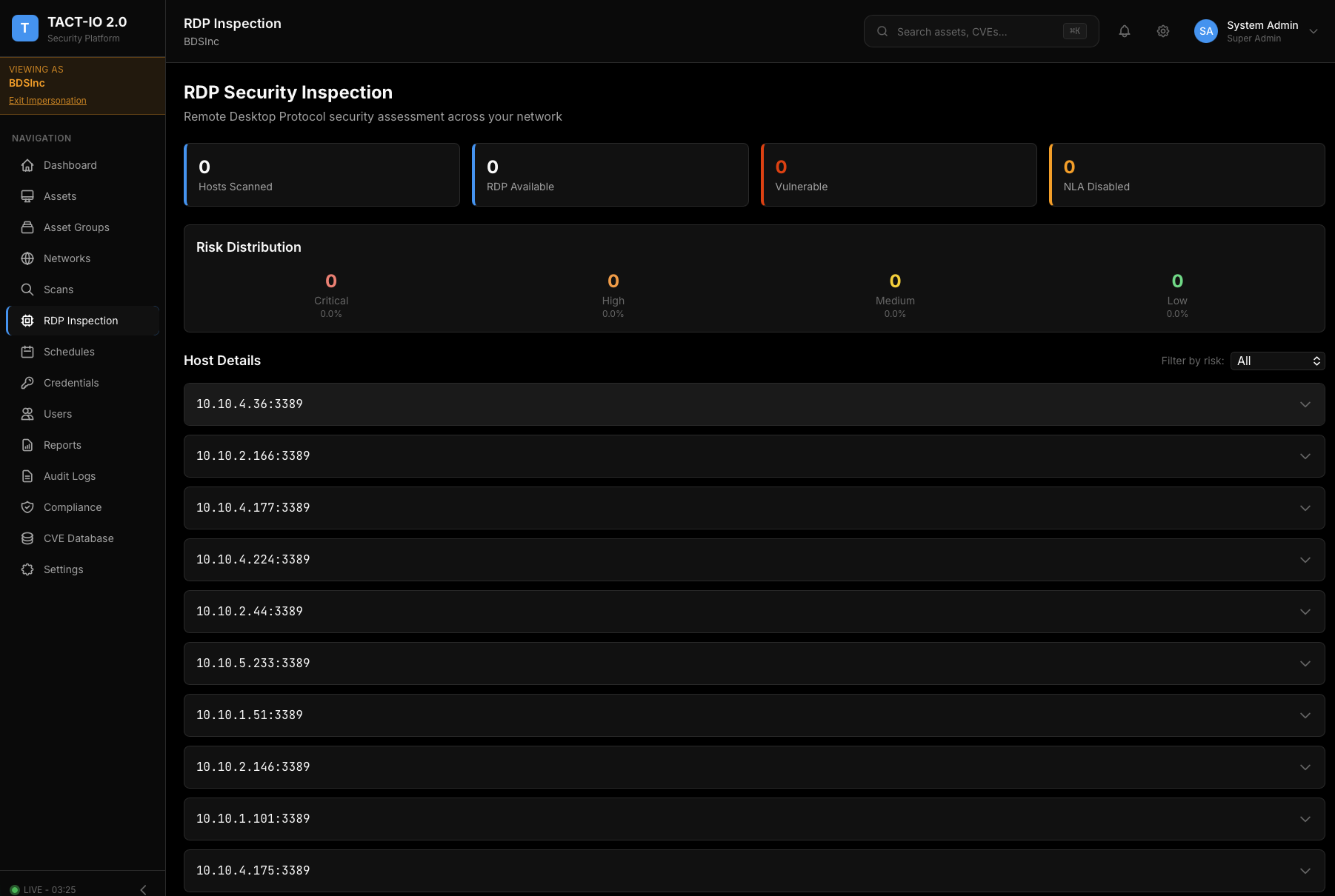
RDP Security Inspection
Deep security assessment of Remote Desktop Protocol services across your network. Identify encryption weaknesses, NLA configuration issues.
Compliance Without Complexity
Stop treating compliance as a point-in-time audit. TACT-IO provides continuous compliance monitoring against major frameworks. Reduce compliance preparation time by 70%.
CIS Benchmarks
100+ platforms
NIST CSF
Full framework
PCI DSS 4.0
All requirements
HIPAA
Complete controls
SOC 2
All criteria
ISO 27001
Full mapping
Automated Evidence
Proof for auditors, automatically gathered
Gap Analysis
Know exactly what needs fixing
Trend Reporting
Track improvement over time
Audit-Ready Reports
One-click documentation generation
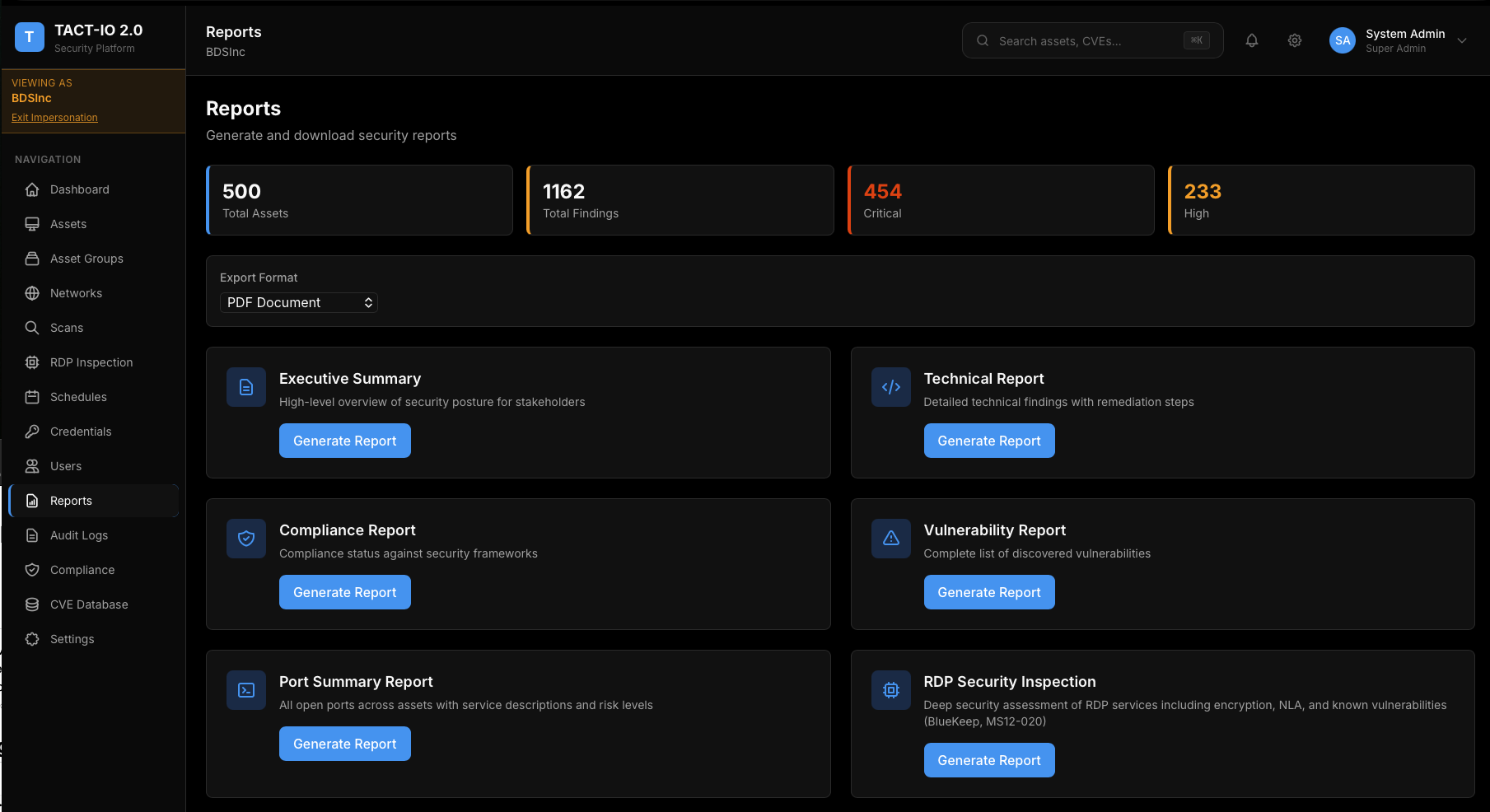
Executive & Technical Reporting
Generate stakeholder-ready reports in seconds. Executive summaries for leadership, technical details for remediation teams, compliance documentation for auditors.
Quick Facts
116+
API Endpoints
6
Compliance Frameworks
<30min
Deployment Time
80%
Fewer False Positives
99.9%
Platform Uptime
24/7
Enterprise Support
Part of the ThreatHunter.ai Ecosystem
TACT-IO integrates with the ARGOS platform and feeds directly into our 24/7 threat hunting operations.
ARGOS Platform
The backbone of all ThreatHunter.ai services. Vulnerability data flows into the same platform our hunters use daily.
GEIGER Attack Paths
Combine vulnerability data with attack path analysis to understand which vulnerabilities actually lead to compromise.
24/7 Threat Hunting
Our hunters use TACT-IO findings to prioritize investigations and identify active exploitation of known vulnerabilities.
Frequently Asked Questions
What is the Real Risk Score?
The Real Risk Score combines seven intelligence sources — CVSS, EPSS exploit probability, CISA KEV status, exploit availability, asset criticality, network exposure, and vulnerability age — to surface the 5% of vulnerabilities that pose 95% of your actual risk.
How does TACT-IO reduce remediation workload?
By prioritizing vulnerabilities based on real-world exploitability and business impact rather than CVSS alone, TACT-IO typically reduces critical findings by 95%, letting teams focus on what actually matters.
What compliance frameworks does TACT-IO support?
TACT-IO supports CIS Benchmarks, NIST CSF, PCI DSS 4.0, HIPAA, SOC 2, and ISO 27001 with continuous monitoring and automated evidence collection.
How quickly can TACT-IO be deployed?
TACT-IO can be deployed in under 30 minutes. Distributed scanners connect to your network with no infrastructure changes required.
Stop Reacting. Start Anticipating.
Experience the full power of TACT-IO with a 30-day free trial. Full platform access, unlimited scans, all integrations enabled.