AI-Powered Identity Threat Detection
MILBERT — Machine Intelligence Learning-Based Enterprise Risk Tracker
The First Agentic AI That Stops Identity Attacks Before They Happen
218,000 authentication events per second. Zero false positives. MILBERT detects the attacks that bypass MFA, steal sessions, and compromise identities.

MFA Was Never Designed for This
Modern attackers do not break MFA. They wait for your users to complete it, then steal the session token. Your identity provider logs a successful login. Your SIEM sees nothing unusual. Your EDR has no endpoint artifacts to detect. Meanwhile, the attacker has persistent access to your environment.
Your current security stack has a blind spot. Attackers know it.
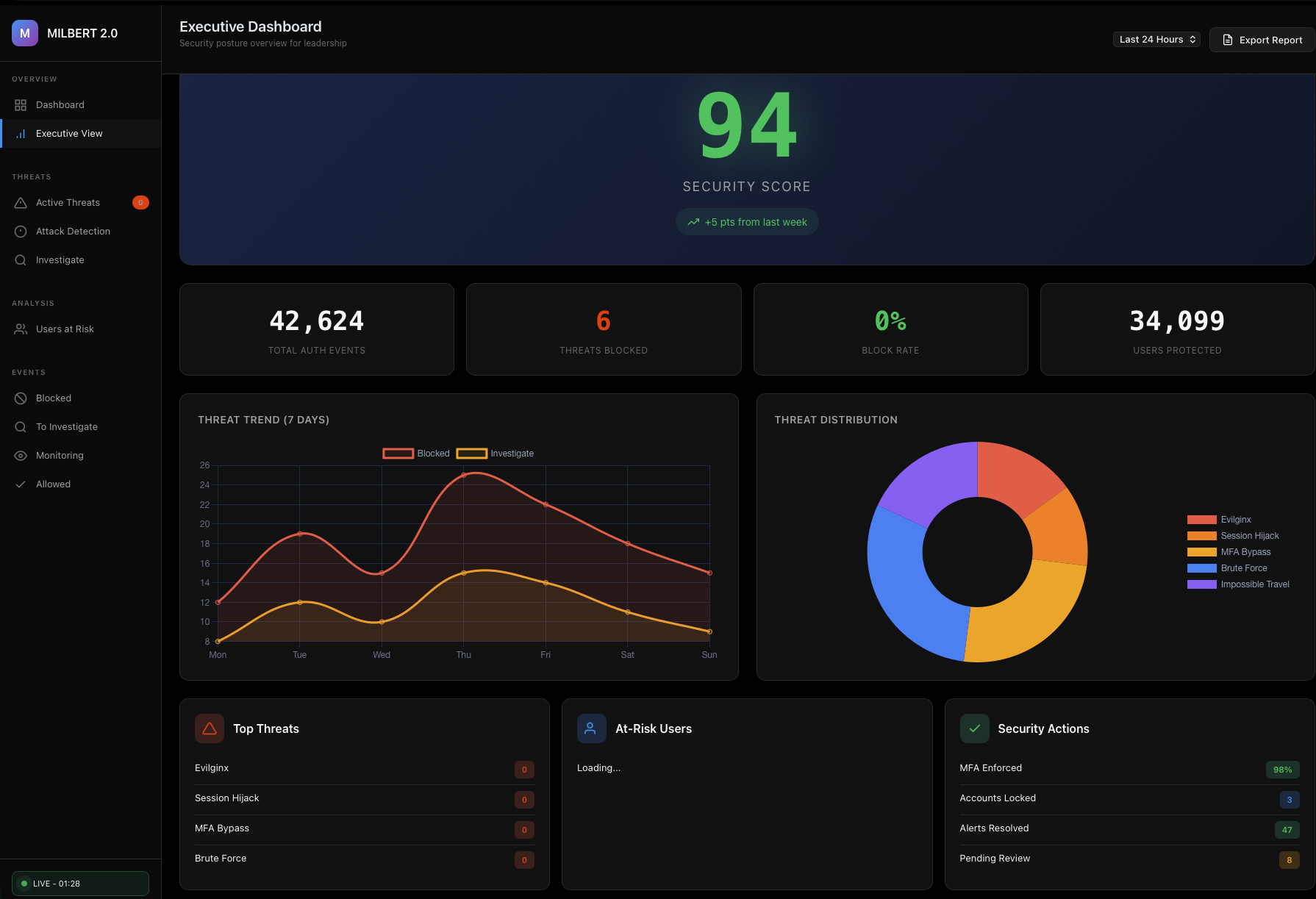
Complete Visibility. One Dashboard.
Security posture at a glance. Overall security score, threat trends, attack distribution, and the metrics your leadership needs.
Complete Identity Threat Coverage
MILBERT analyzes every authentication event in real-time, combining behavioral analytics, threat intelligence, and session tracking to detect attacks the moment they happen.
AiTM and EVILGINX Attacks
Phishing that captures session tokens after MFA completion. MILBERT detects MFA satisfied by token claim without fresh authentication, unbound token protection, and multi-signal patterns that indicate credential theft.
Session Hijacking
Stolen tokens used from multiple locations or devices. MILBERT tracks session behavior and flags when the same session appears from different IPs, different devices, or with geographic anomalies.
Impossible Travel
User authenticating from New York at 9:00 AM and Moscow at 9:15 AM. MILBERT calculates geographic feasibility using precise distance and time analysis.
Brute Force and Password Spray
Automated credential attacks. MILBERT identifies patterns across failed authentication attempts, detecting both high-volume attacks against single accounts and distributed attacks across multiple users.
MFA Bypass and Downgrade
Attacks that circumvent or weaken MFA requirements. MILBERT monitors for conditional access policy failures and authentication requirement downgrades.
Token Replay
Stolen tokens reused beyond normal session behavior. MILBERT tracks usage patterns and flags excessive reuse, unexpected locations, or suspicious timing.
Bot and Automated Attacks
Non-human authentication attempts. MILBERT identifies suspicious user agents, high-frequency patterns, and attempts from datacenter infrastructure.
Off-Hours Access
Authentication outside established patterns. MILBERT learns when each user typically works and flags access during unusual hours.
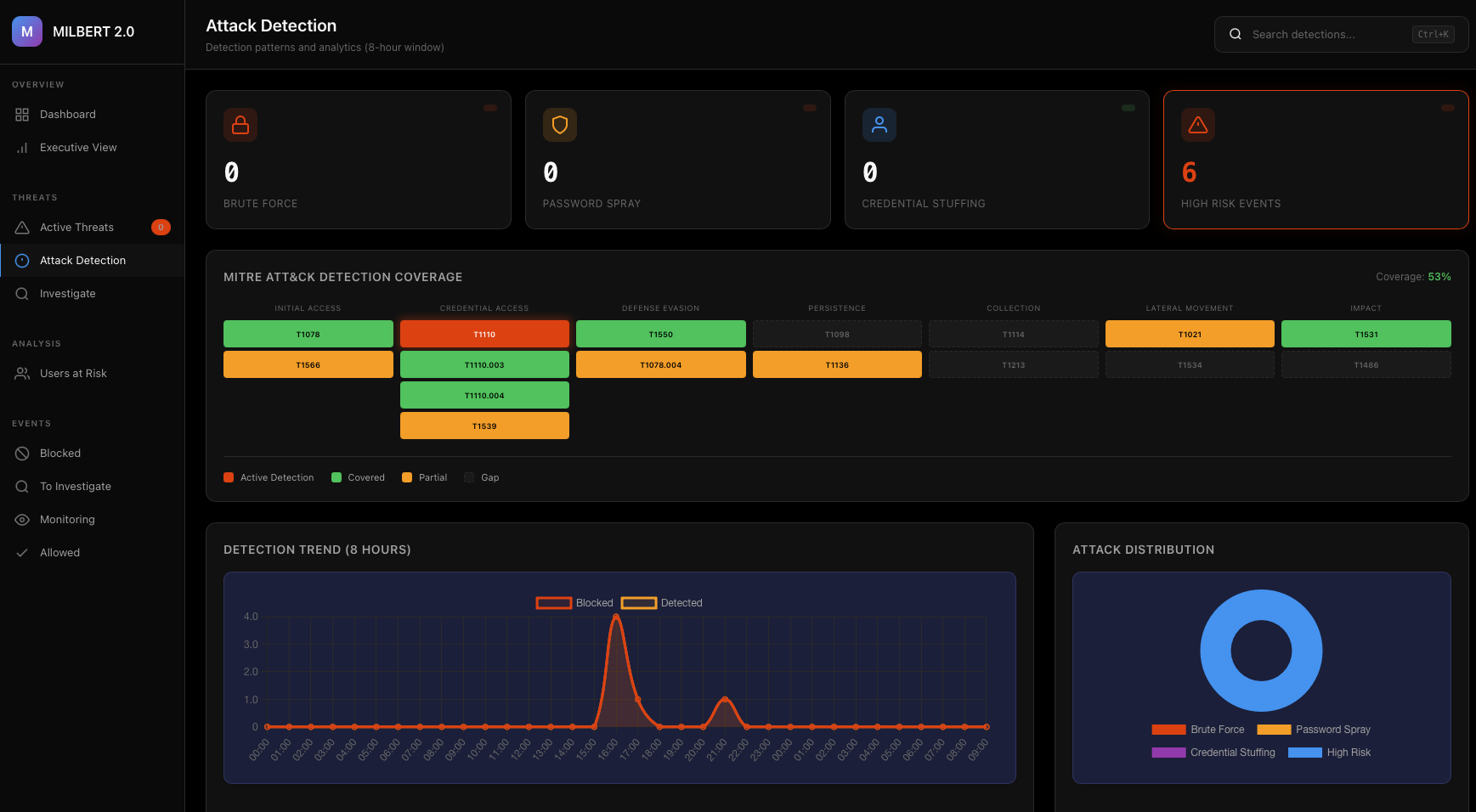
MITRE ATT&CK Coverage
Detection capabilities mapped to industry standards. See active threats by category, detection trends, and attack distribution across your environment.
Initial Access
- T1078 Valid Accounts
- T1566 Phishing
Credential Access
- T1110 Brute Force
- T1110.003 Password Spraying
- T1110.004 Credential Stuffing
- T1539 Steal Web Session Cookie
Defense Evasion
- T1550 Use Alternate Authentication Material
- T1078.004 Cloud Accounts
Persistence
- T1098 Account Manipulation
- T1136 Create Account
Lateral Movement
- T1021 Remote Services
- T1534 Internal Spearphishing
Three Steps to Identity Protection
Connect
Integrate with your identity provider in minutes. Azure AD (Commercial and GCC High), Okta, Google Workspace, Duo, Salesforce, and GCP. No agents. No network changes.
Learn
MILBERT builds behavioral baselines for every user. Locations, devices, access patterns, timing. Continuous adaptation as your organization evolves.
Protect
Every authentication analyzed in real-time. Risk score calculated in milliseconds. High-risk events blocked automatically. Suspicious events flagged for investigation.
What Your Current Tools Miss
Your SIEM collects logs but lacks context. Your MFA provider confirms authentication but has no visibility into session behavior afterward. Your EDR watches endpoints but identity attacks that move cloud-to-cloud never touch an endpoint. MILBERT fills the gap.
| Challenge | Traditional Approach | MILBERT |
|---|---|---|
| Detect MFA bypass | Cannot - MFA shows "success" | Multi-signal AiTM detection |
| Impossible travel | Manual log correlation | Automatic geographic analysis |
| Session hijacking | Invisible to most tools | Real-time session tracking |
| Investigation time | Hours across multiple consoles | Seconds in unified dashboard |
| False positives | Alert fatigue | Behavioral learning reduces noise |
| Token replay | No visibility | Usage pattern tracking |
Every Authentication Scored in Milliseconds
MILBERT combines multiple signals: geographic risk, device trust, behavioral analysis, threat intelligence, session characteristics, and attack pattern detection.
Thresholds configurable per organization based on risk tolerance.
Works With Your Stack
Cloud-hosted or on-premises. No agents required. Multi-tenant capable.
MILBERT operates as an analysis layer. Your authentication infrastructure remains unchanged.
Part of the ThreatHunter.ai Ecosystem
MILBERT is powered by the ARGOS platform and backed by expert threat hunters who monitor your environment 24/7/365.
ARGOS Platform
The backbone of all ThreatHunter.ai services. Unlimited data sources, real-time processing, and AI-powered analysis.
24/7 Threat Hunting
Human analysts with military and intelligence backgrounds actively hunt for threats that automated tools miss.
GEIGER Attack Paths
Combine identity threat detection with attack path analysis to see the full picture of your security posture.
Frequently Asked Questions
What attacks does MILBERT detect?
MILBERT detects AiTM and Evilginx phishing, session hijacking, impossible travel, brute force, password spraying, MFA bypass and downgrade, token replay, bot attacks, and off-hours access anomalies.
How does MILBERT handle false positives?
MILBERT builds behavioral baselines for every user and organization, resulting in zero false positives. Each alert represents a genuine threat that warrants investigation.
How quickly can MILBERT be deployed?
MILBERT connects to your identity provider in minutes with no agents or network changes. It supports Azure AD (Commercial and GCC High), Okta, Google Workspace, Duo, Salesforce, and GCP.
Does MILBERT replace my existing MFA or identity provider?
No. MILBERT operates as an analysis layer on top of your existing authentication infrastructure. Your MFA, identity provider, and security policies remain unchanged.
See MILBERT in Action
Start your free 90-day trial or request a demo to see how MILBERT protects your organization from identity attacks in real-time.